Software capabilities
Reporting by direct connection
Each of the systems in red light violation enforcement system, are able to directly connect to the network in web-based mode. Therefore, in addition to the mechanisms of the expanded monitoring centers, it is possible to monitor the performance of every single system as well. For this purpose, just enter the system’s IP into the internet browser and after the confirmation of the access level and the corresponding password, the system status, statistical reports and access to violations will be provided to the user. The application of this feature is impressive in monitoring and maintaining the systems.
Reports on alternative network platforms
The red light violation enforcement system is equipped with a cellular communication system which is specifically designed for this system, and in the event of any danger, including the unauthorized opening of doors without an electronic key or hard blows, the related alert message will be immediately transmitted to the monitoring center through the communication platform (fiber or any network-based platform which is considered for the project).
The system is also capable of sending SMS-based alerts. In case of potential hazards and unauthorized access, an SMS, containing the location of the camera and the type of occurring danger, will be immediately sent to the responsible person. It is also possible to use the SMS to inquire about the general status of the system, which is very practical for the monitoring and maintenance personnel.
The ability of automatic troubleshooting
The electronic board designed especially for the red light violation enforcement system will automatically check and detect the faults in different parts of the system, and if there is any problem, it automatically solves the problem. As a result, in order to maintain the continuous and 24/7 functionality of the red light violation system, the monitoring board continuously monitors the performance of the system and resolves the problems, as far as possible.
The application of the watchdog method is implemented in order to control the software and processor parts, and so, even if there is an error in the system or any kind of software failure which disturbs the system’s functioning, the electronic board will automatically reset or turns the system on and off.
Management and reporting software
Generally, there are non-processing and interfacing software which is implemented in all over the city systems, as well as the software which are installed on the central server and provide services to all types of network users.
Considering the way of applying the system, the overall system view and user units are as follows:
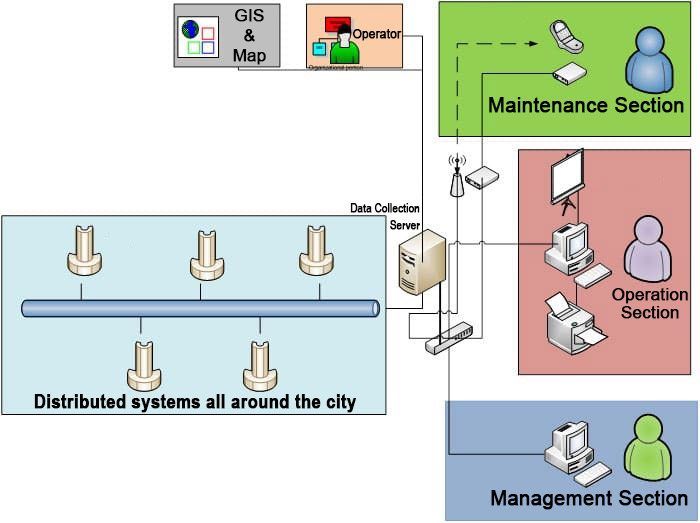
The tasks of non-processing software on each side of the pole are as follows:
- Recording and storing the traffic information in the database
- Communication with electronic boards and monitoring the status of equipment and sensors
- Application of the SMS module in order to report the status and failures
- Transferring information to the center
- Data logging in a local way for offline usage and periodic system testing
- Providing web-based reports and statistics
The central software has the following sections:
Management section
- Definition of user categories, access levels, and the related setting
- Determination of camera groups for each axis
- Definition of camera settings groups
- View logs
- Settings related to the initiation of the software lock
- Definition of cellphone number for maintenance operators in order to send SMS
Operation section
- Observing the unconfirmed images (there should not be any access to the violations for which a penalty paper has been issued, as well as old violations)
- The ability to modify the vehicle’s license plate and confirmation of the violations’ images. The verified information would be stored in the database along with the operator’s name. Also, a barcode and a tracking code would be generated for each violation.
- Preparation of the operation log including entrance and exit times and the number of daily operations.
- Separation of non-verifiable images in a specific folder as well as storing in a database for statistical reports with associated usernames
- Determination and completion of a violation in an image if the system has done it incompletely.
- Assigning the system status code to each of the images (for example, if the image is related to a system which has a faulty flash, this item would be stored for this violation with a specific code).
- The possibility of printing the verified violations (the software must intelligently avoid errors such as printing multiple copies or not printing an image.)
Maintenance section
- The possibility of defining components’ lifetime
- Provide definitive reports and system defectives
- Alarm notification of failure or camera disconnections
- Alarm for the end of a piece’s lifetime
- Monitoring the current status of each system
- Alarms for maintenance services and calibration of the cameras
- Preparation of performance log for the maintenance operators
- Sending SMS to maintenance operators based on defect definition and management settings
- The possibility of functioning via modem and telephone line
- Storing the records of failure events and modification of it for later reporting
- The ability of performance and overall system test (processor, camera, flash, SMS, etc.)
Offline and online statistics, and reports section:
- Providing comprehensive statistical reports of system information
- Copying, aggregating and integrating cameras’ data
- Providing useful graphs of operators
- Preparing reports in standard formats, including Excel
- The input of the standard format capabilities from the police law enforcement system in order to complete the reports
- Preparing real-time traffic statistics reports on GIS platform in color and providing a standard text file of the IIS port in order to transfer to an I-map existing in the Traffic Control Center
- Providing online statistical reports with the ability to submit on a website
- The ability to send the whole real-time online information which results in a crisis, such as too much traffic
The overall architecture of these sections is as follows:
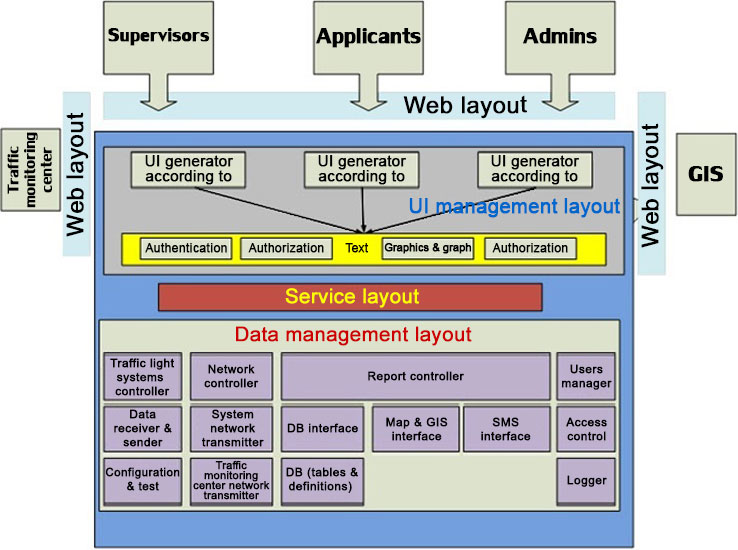
It should be noted that the above design is a preassumption for the main design and according to the technical attachment, the outputs associated with the user groups will be applied to define the features of this software in a customized way.
